Connecting to iDRAC VPN by using L2TP over IPsec on Fedora Linux 30
Table of contents
The integrated out-of-band management platform on Dell servers is called iDRAC. By default, access to the iDRAC interface of your servers is provided via a VPN. This guide explains how to access iDRAC using a VPN.
Alternatively, if necessary, you can enable temporary public access to the iDRAC interface, allowing access without a VPN. This can be activated in the customer portal through the server details page under the OOB section by selecting Enable public access for 24 hours. Once activated, public access remains enabled for the next 24 hours, but can be manually disabled at any time.
For security reasons, VPN access remains the preferred method and should be used whenever possible.
Finding VPN credentials
Credentials for setting up a VPN connection to the OOB network and instructions are available in the customer portal. To access them:
- Navigate to Networks → VPN access → VPN to DRAC section
- Select the location and click Credentials
- In the opened window, you will find the credentials:
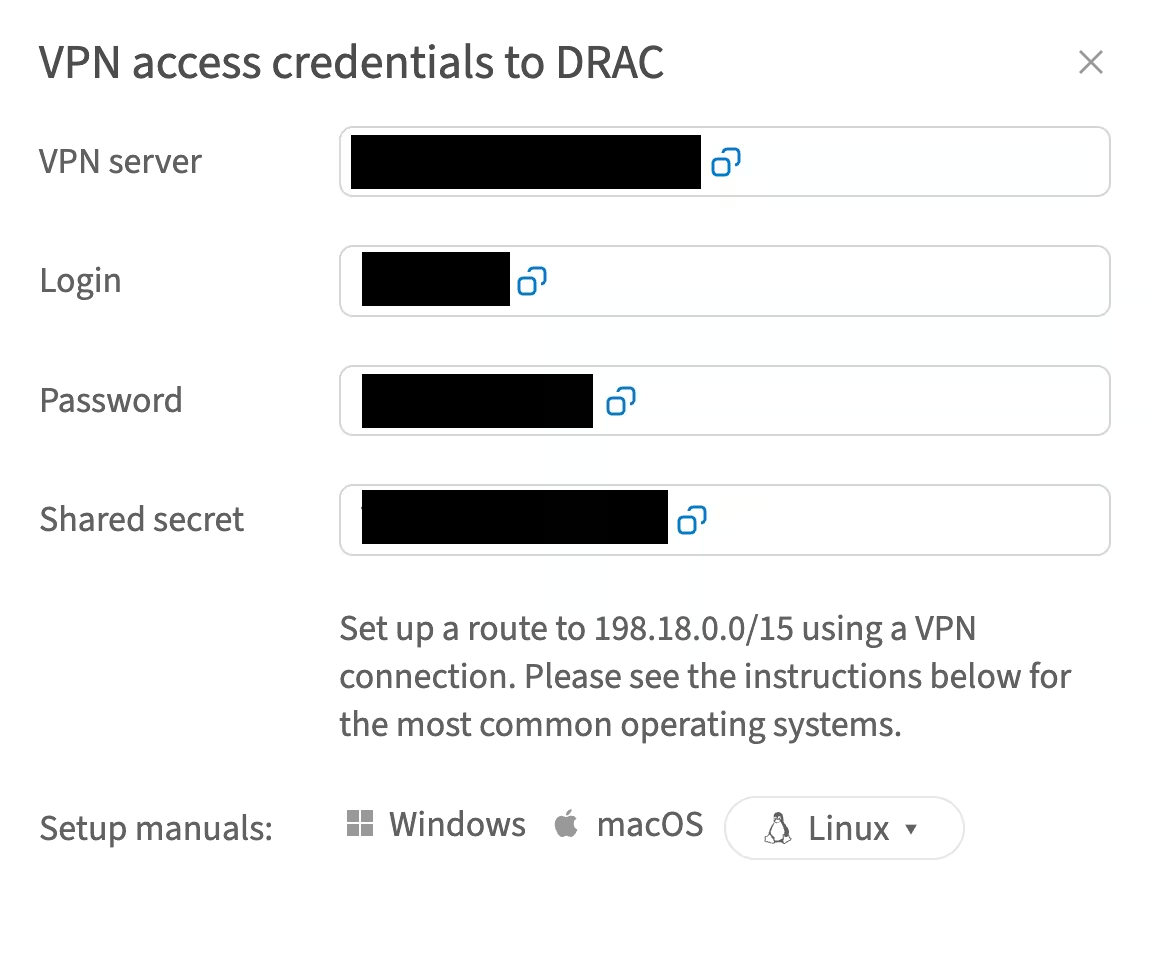
Installing required packages
- Update the package information to retrieve the latest versions and dependencies:
sudo dnf update - Install the L2TP plugin for NetworkManager:
sudo dnf install NetworkManager-l2tp NetworkManager-l2tp-gnome -y - Restart your system:
sudo reboot
Setting up a new VPN connection
- Click the Settings button in the shortcuts menu:
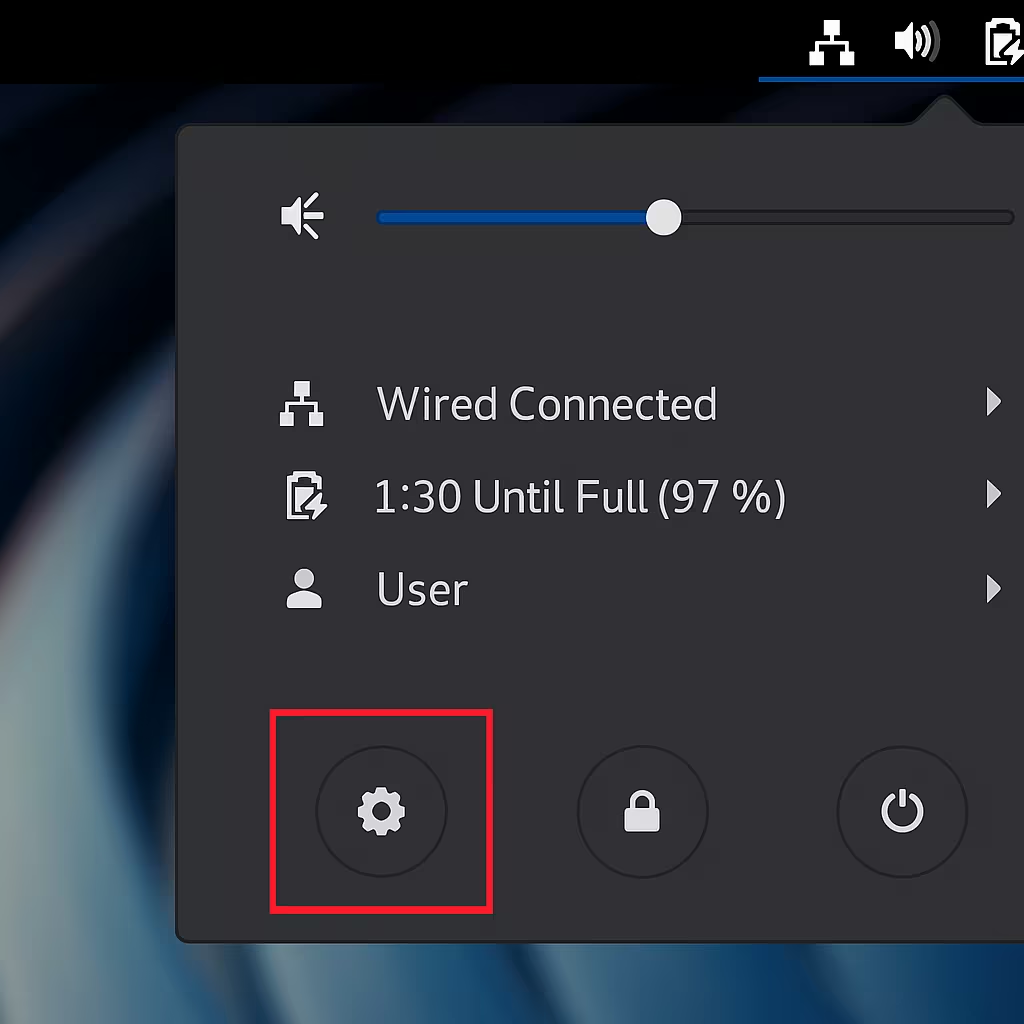
- In the Settings window, navigate to the Network tab and click the "+" button next to the VPN label to add a new VPN connection:
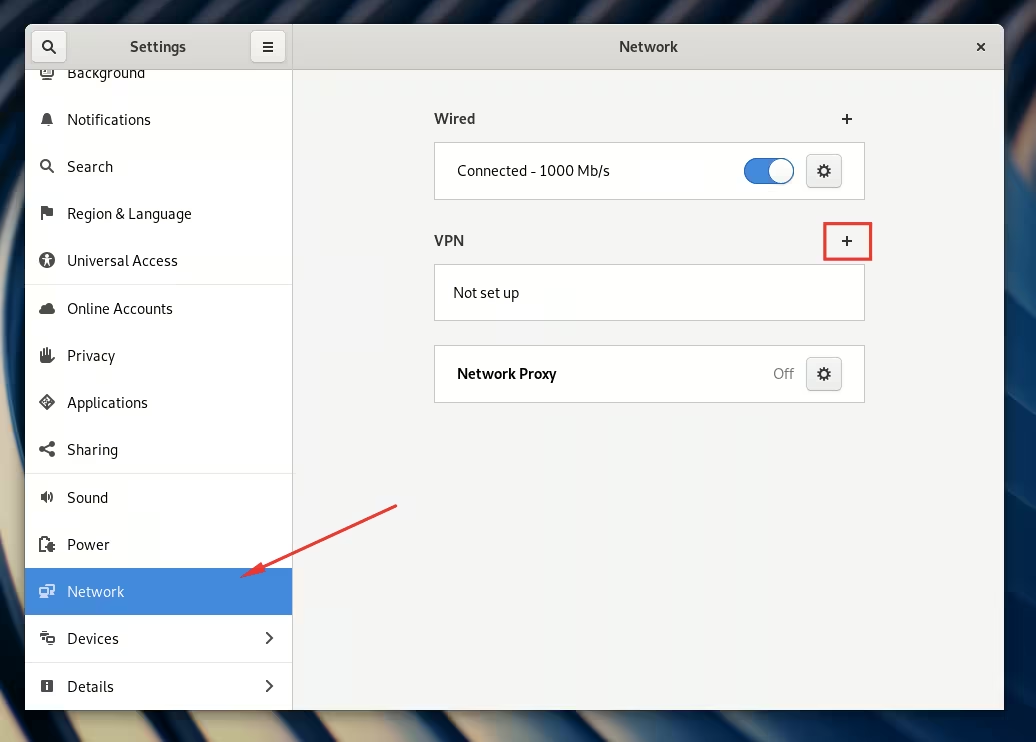
- Choose Layer 2 Tunneling Protocol (L2TP):
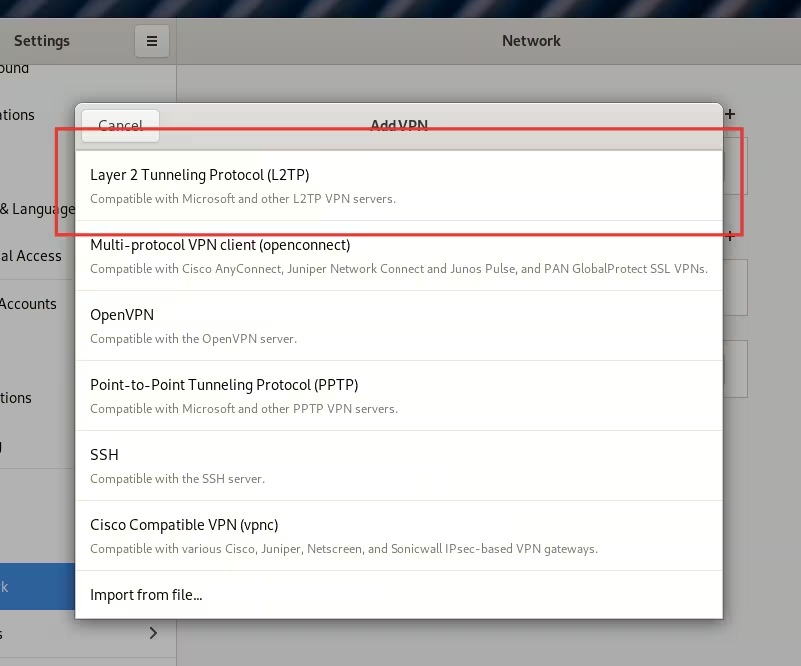
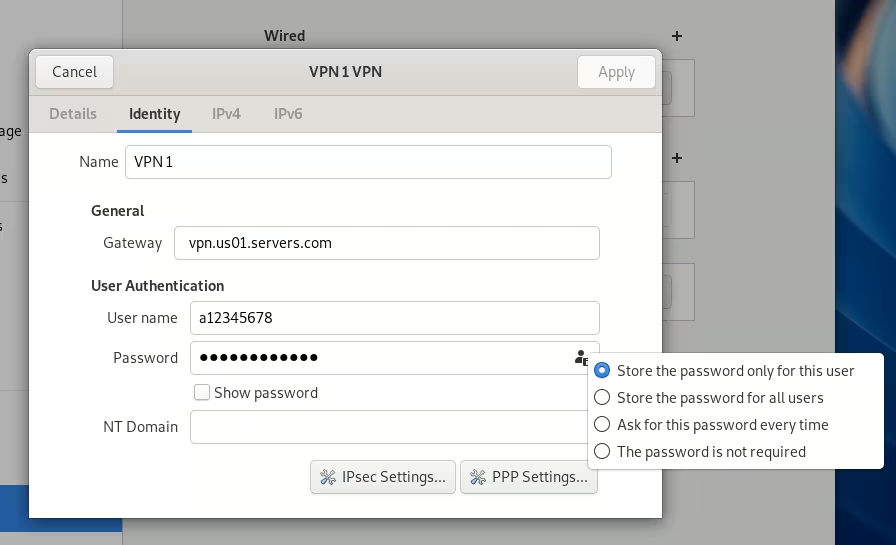
- In the VPN connection settings, go to the Identity tab and enter the following details:
- Name (e.g. VPN1)
- Login credentials obtained from the customer portal:
- Gateway - VPN server
- Username - Login
- Password - Password
- Click the user symbol in the password input field and select Store the password only for this user:
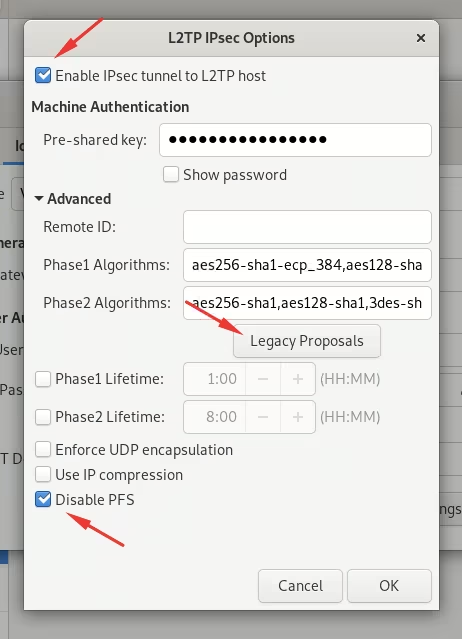
- In the same tab, click IPsec Settings and proceed with the following steps:
- Tick Enable IPsec tunnel to L2TP host
- Enter the shared secret obtained from the customer portal in the Pre-shared key input filed
- (Optional) Click Legacy Proposals to auto-fill the required fields or manually specify the encryption methods. A full list of supported methods can be found here: Supported tunnel options
Example configuration:- Set Phase1 Algorithms to
aes128-sha1-modp2048 - Set Phase2 Algorithms to
aes128-sha1
- Set Phase1 Algorithms to
- Tick Disable PFS, then click OK
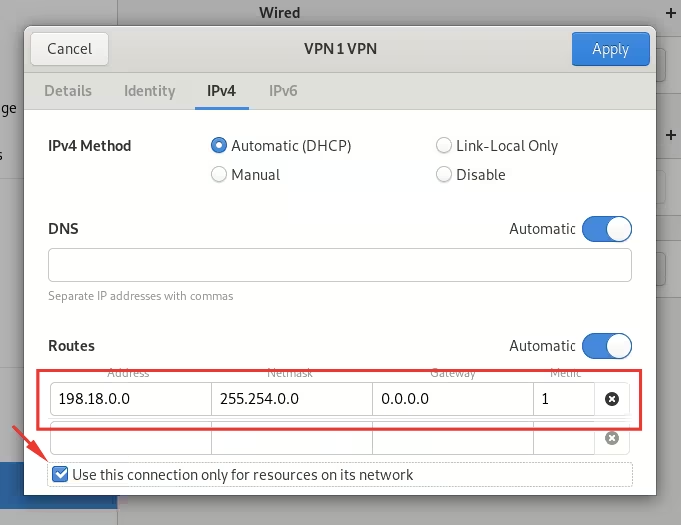
- Navigate to the IPv4 tab and scroll down to Routes:
- Add the following routes:
198.18.0.0100.64.0.0
- Click Apply to save the settings
- Add the following routes:
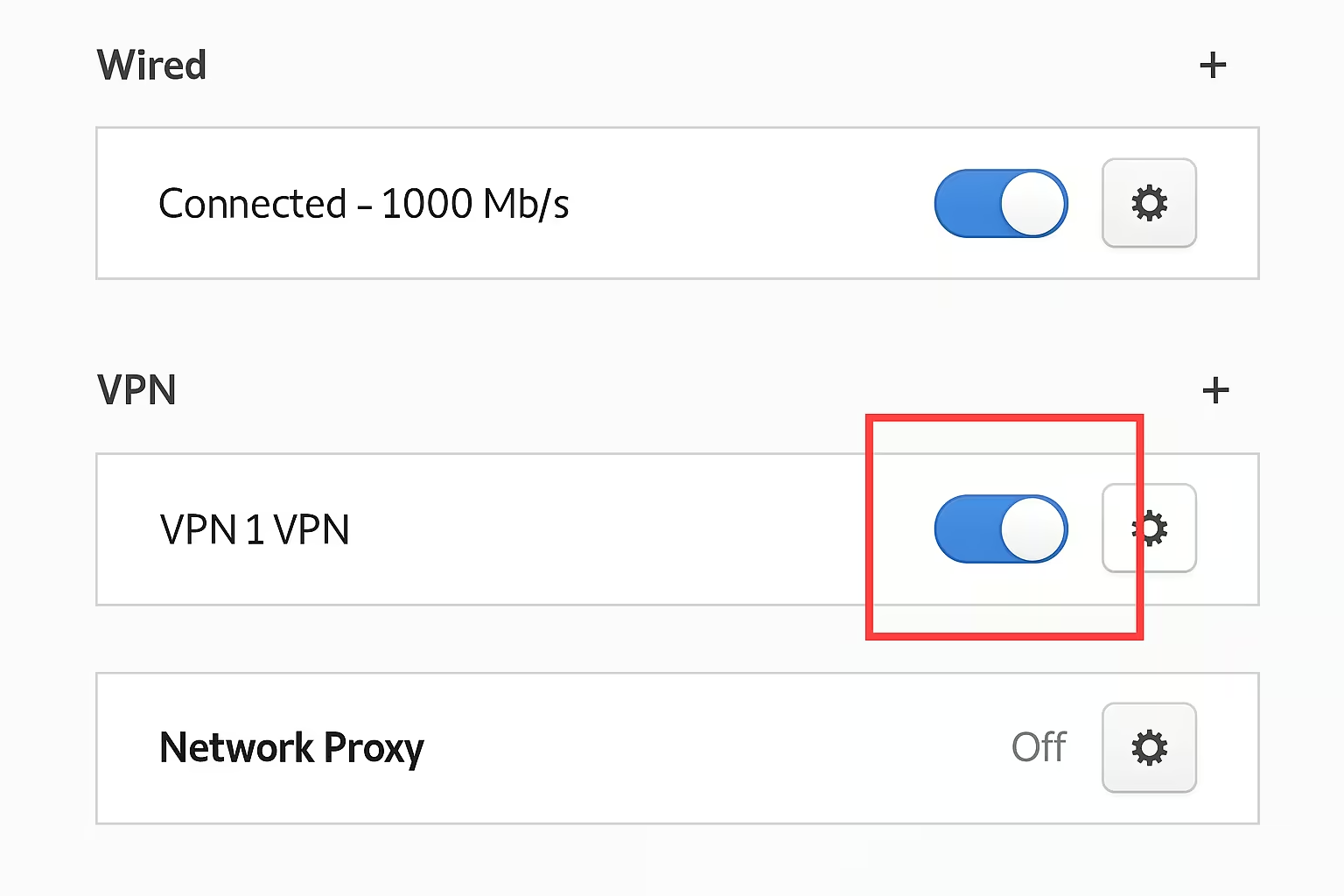
- Ensure your newly created VPN connection is turned on:
Finding iDRAC credentials
The IP address and credentials for an individual server's iDRAC interface can be found in the customer portal:
- Navigate to Dedicated Servers → Manage → Your server → Details
- Scroll to the OOB section and click Credentials